Friday night has come, the workweek has passed, and you sit down to enjoy a night of games… only for the servers to be down. Distributed Denial of Service attacks are a frustrating experience that most gamers in the modern age can relate to in some capacity. That big release night, the random weekend, or even a personal attack against a server you own.
Today we will be looking back over the history of DDoS attacks and how they evolved into an online weapon of modern-day misery.
What is a DDoS Attack?
Before diving in, it is best to understand what exactly a DDoS is. DDoS attacks, or Distributed Denial of Service attacks, are an attempt to flood one or more servers with requests which in turn overloads them.
An analogy one can use is of a highway. Under normal circumstances, everyone can travel down the highway without issue, but all of a sudden, someone’s army of self-driving cars are all trying to use the highway at once. Traffic is at a standstill, the self-driving cars keep coming, and legitimate drivers are stuck trying to make it through the chaos.
All the while, authorities can’t stop or find who is sending the cars because they are leaving from multiple parking lots and using every on ramp the highway has.
What is the goal of a DDoS Attack?
DDoS Attacks have been used for many purposes including activism, but in the context of gaming servers, the answer is to inconvenience you, the paying customer. The attacker, or the person who hired someone to make the attack, gains absolutely nothing. It is an illegal act done for the sole purpose of wasting other people’s time.
Are DDoS Attacks legal?
DDoS attacks are illegal in many jurisdictions such as Canada, the United States, and the United Kingdom. The penalties being as significant as ten years in prison if caught. Unfortunately, “if caught” needs to be emphasized.
DDoS Attacks come from multiple locations, and when combined with the perpetrator using proxies and VPNs, it can be tough to find the true origin. Even in more minor cases where an individual may know who made the attack, there is often little local authorities can, or are willing, to do. It is for these reasons DDoS attacks remain so common with so few arrests.
Evolution of DDoS
The earliest recorded denial of service attack took place against the internet service provider Panix on September 6, 1996. The type of DoS used was called an SYN flood which is done by rapidly creating multiple connections while finalizing none of them. This overloads a server with half-opened connections.
Later the following year, a DDoS demonstration would take place by Khan C. Smith at DEF CON, a hacker convention, in which he left the Las Vegas Strip without internet access for over an hour. The release of sample code from that same event would lead to a series of DDoS attacks against multiple major corporations in the year that followed.
DDoS attacks have continued to evolve since then, but true to their origins, they are still used to disrupt corporations and their customers to this day. Game servers included.
Types of DDoS Attacks Against Game Servers
There are many types of DDoS attacks, but the kind most commonly seen against gaming servers are Application Layer Attacks, also known as Layer 7 DDoS Attacks, and volumetric DDoS attacks.
Layer 7 sends more requests to a server application than it can handle, which in turn overloads the server leaving it unable to recover until the attack ends. Due to ease of use and low resource requirements, Layer 7 is generally the more common of the two with a quarter-on-quarter increase of 573% reported just last year.
Volumetric attacks are made by sending more traffic to a network than it can handle. This type of attack can be seen in real-time in the form of mass bot login attempts. Last year Cloudflare thwarted the largest known volumetric attack to date which was recorded to have reached 17.2 million requests-per-second. One of many attacks by the infamous Mirai botnet.
How common are DDoS Attacks against game servers?
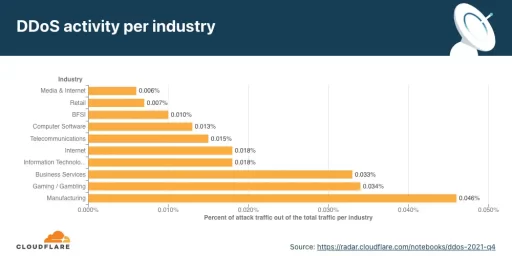
Cloudflare’s DDoS Attack trends for Q4 2021 reported a staggering 29% year-on-year increase in Ransom DDoS attacks. A DDoS where the attacker first threatens a server owner or sends a ransom letter.
Additionally, Cloudflare reported the Gaming industry was the second most targeted industry with Layer 7 DDoS Attacks. This made up an astounding 0.034% of the industry’s total traffic for the fourth quarter of 2021.
Protecting Your Game Server From DDoS Attacks
DDoS Protections and DDoS Attacks are continuously evolving to gain the upper hand in a never-ending battle. This leaves protection methods quickly outdated, but there are still effective measures that can be taken to protect one’s Game Server.
For example, firewalls can act as gatekeepers identifying insincere traffic and requests to prevent a DDoS attack before it even begins. However, even firewalls have limits, and the attack’s size can overrun the defenses in place.
Proxy servers acting as a buffer can also assist in the protection of a dedicated game server by mitigating DDoS attacks. This is to a much lesser extent than firewalls, however.
Dedicated server hosting will generally include built-in DDoS protection with a set bandwidth, leading us to our last point.
Choosing a Game Server Host That Will Go the Extra Mile to Protect You
The built-in DDoS protection offered by game server hosts can be very low or non-existent in some cases. A convenient way to save money, assuming there are no DDoS attacks.
When purchasing a game server, make sure it is from a host that is willing to go the extra mile to protect you. It may not be listed publicly, so do not be scared to reach out to a company’s livechat or ticket support for the specifics of their DDoS protection.
Stay safe, have fun, and never respond to DDoS ransoms or threats.
Until Next Time,
MelonCube